November 22, 2018 • Garrett Garitano
Are You Using the Best CAPTCHA for Online Security?
CAPTCHA is the name for online tools that distinguish between humans and bots. You’ve likely used a CAPTCHA when filling out a web form, or the CAPTCHA may have authenticated you behind the scenes without you realizing it. Here’s what you need to know about how CAPTCHA helps online security. What Is CAPTCHA? CAPTCHA is […]

CAPTCHA is the name for online tools that distinguish between humans and bots. You’ve likely used a CAPTCHA when filling out a web form, or the CAPTCHA may have authenticated you behind the scenes without you realizing it.
Here’s what you need to know about how CAPTCHA helps online security.
What Is CAPTCHA?
CAPTCHA is an acronym that stands for “Completely Automated Public Turing test to tell Computers and Humans Apart.”
The challenge-response system acts as a gatekeeper for web forms, blog comments, and other content interactions. The authentication process of CAPTCHA improves security by deterring bots that generate automated content and hackers who insert malicious code.
The security methodology dates back to 1997 when the leading search engine, AltaVista, needed a way to deal with automated URL submissions that were skewing its search engine rankings. The solution devised by the company’s chief scientist was an embedded application that generates an image of a random text sequence. Because computers couldn’t read the text, the tool filtered out bots.
Impacts of CAPTCHA
The development of CAPTCHA technology and its further refinement over the years have had a significant impact on how the internet handles spam.
In one analysis, CAPTCHA reduced spam by 88 percent. Extrapolate that out across 21 years of internet history to consider where we’d be today without this authentication tool.
However, CAPTCHA technology can also affect usability. Humans may struggle to complete a CAPTCHA and need multiple attempts before authentication. Some businesses have found that the presence of a CAPTCHA on a web form can negatively affect conversion rates by 3.2 percent, which is a big deal in businesses with tight margins.
This experience of failing a CAPTCHA authentication can feel similar to trying to walk into a store through an automated door that doesn’t open for you. It’s the web equivalent of these Star Trek bloopers. On the other hand, a fully functioning security authentication system is similar to this elegant installation of automatic doors at Dutch Design Week.
7 Types of CAPTCHA
Below is a list of the most common types of CAPTCHA, starting with lo-fi methods going through high-tech, cutting-edge ways to determine that the user is human.
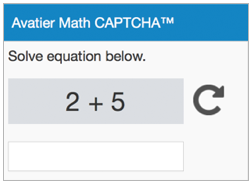
- Math CAPTCHA: Asking a user to solve a simple math problem such as “2+5” is one of the simplest forms of authentication.
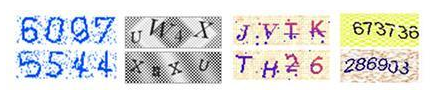
- Alphanumeric CAPTCHA: This CAPTCHA displays a text string of letters and numbers within an image, and users must enter the characters they see. Visually impaired users typically have an audio alternative of the same text string.

- Image CAPTCHA: Implemented in 2014, image-based authentication is where users are shown a grid of nine images and must select all of the cats, street signs, storefronts, or other visuals.

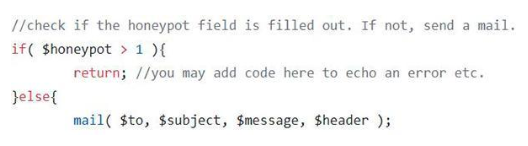
- Honeypot CAPTCHA: This authentication method isn’t seen by users and doesn’t need any interaction from them. Instead, it tricks the bots by using hidden fields that humans cannot see. Because bots are typically programmed to automatically fill out the forms, a completed form causes de-authentication.
- reCAPTCHA v2: Released by Google in 2014, this authentication requires only a single click to a checkbox that reads, “I am not a robot.” Otherwise known as “No CAPTCHA reCAPTCHA,” the authentication works by tracking a user’s cursor movements. A click directly in the center of the box could indicate a bot whereas a human would likely not click at the exact midpoint.
- Invisible reCAPTCHA: In 2017, Google released a way to use reCAPTCHA v2 technology within existing page interactions. So, instead of a separate “I am not a robot” button, the tool lets you programmatically bind the technology within an existing checkbox, such as “subscribe to my newsletter.”
- reCAPTCHA v3: Just released in October, reCAPTCHA v3 is a Java API that doesn’t need user interaction to authenticate that the user is human. Instead, the behind-the-scenes algorithm generates a user score based on the interaction so you can determine actions such as automated authentication, requires moderation, or flag as spam.
How Successful Are CAPTCHA at Security?
Due to advanced machine learning and the increased sophistication of bots, CAPTCHA methodologies are most successful when they stay one step ahead of the spammers.
For example, early alphanumeric CAPTCHAs that were a short string of five numbers on a black background image are now crackable at a 100 percent success rate.
This led to creating CAPTCHA images with increasing complexity of the numbers being overlaid on a field of visual noise. This made it more difficult for bots to “read” the text string.
This style was followed by today’s alphanumeric CAPTCHAs where the text string is warped and distorted, making it more difficult for bots to decode the text and bypass authentication.
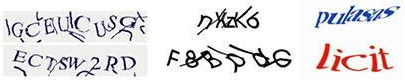
In the case of the notorious ticket scalper scandal, Wiseguy Tickets was able to bypass the CAPTCHA on Ticketmaster and similar sites between 1999 and 2010. According to the FBI’s indictment, this allowed the group to make $25 million in profit, $2.5 million of which was from the 2005 U2 tour alone.
To combat the sophistication of scammers, businesses need to implement security technologies that stay on the leading edge. For example, Amazon recently patented a CAPTCHA idea that tests users understanding of Newtonian physics.
Researchers are working on TAPCHA or mobile-based CAPTCHA technology that demonstrates how context and interaction can be used in combination to authenticate users.
Through security and access innovation, businesses can stay one step ahead of potential threats.
Find out how Avatier, a leader in innovation for identity access management, can help you strike the balance between high security and smooth usability.