You want fast multi-factor authentication, but IT tells you that’s impossible. We’ve heard that story too, and we have some good news. There’s a way to make multi-factor authentication happen quickly. When you have MFA in place, and employees are using it, your organization will become much more difficult to hack. To show how fast multi-factor authentication is possible, take a step back to explore why people view MFA as slow and inefficient right now.
Why Multi-factor Authentication Is Perceived as Slow
Multi-factor authentication has a slowpoke reputation for two reasons. Early versions took a long time to implement. You needed to establish a formal project group, decide to build or buy the system, and start the project. The initial implementation could take months, or longer in the case of large-scale projects. Once the system is in place, the slow speed problems only continued.
Picture this: employees used to require a particular “login device” or token to use MFA. While this hardware login device did make for robust security, there was a significant tradeoff associated with it. If you left the device at the office, at home, or somewhere else, you couldn’t use the system. That’s not all; in most cases, you also needed to submit a formal request for the device in the first place and get manager approval. As a result, few people learned how to use multi-factor authentication. Those who did start to use it often found that it was tough to remember the complex login process.
Introducing the Past to Fast Multi-factor Authentication
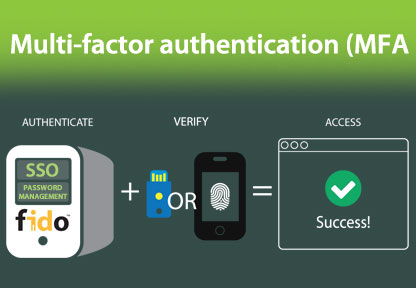
Today, you can bring faster multi-factor authentication to your organization. Security specialists have recognized the need for speed and convenience. Without those critical factors, it’s simply too challenging to get employees to start using multi-factor authentication or otherwise change their security practices. It’s no longer necessary to issue a specific login token or device to each employee. Instead, they can use the technology they already have, such as a smartphone, to authenticate. That’s possible because companies such as Avatier have implemented support for the FIDO2 standard.
With FIDO2 support, you no longer need to buy thousands of authentication tokens and distribute them to your entire workforce. Instead, your employees can use their existing technology. Since most employees already use smartphones, it’s easy for them to adopt the new system. From a project management point of view, this new approach to fast multi-factor authentication is also quick to implement. You only need to purchase and implement Avatier’s identity and access management software solution and choose one of the MFA providers we support.
Getting Your Fast Multi-factor Authentication Solution in Place
For the best results, we recommend you follow these steps to get the most out of your multi-factor authentication (MFA) solution.
1. Align Multi-factor Authentication with Your IT Strategy
Before you commit corporate resources and time to MFA, you need to show how it’s aligned with your strategy. For instance, your company may have a goal to minimize the risk of IT security events. In that case, implementing multi-factor authentication directly contributes to that goal. If you’re not sure how to connect multi-factor authentication to your IT strategy, meet with some other managers in the organization to seek out their perspective.
2. Choose Your Authentication Factors
To translate multi-factor authentication from theory to life, you need to make some choices. Here’s a popular multi-factor authentication approach: password plus smartphone authentication. When you start, that’s all you need. After your multi-factor authentication is up and running, you can add other authentication factors. For your senior IT security managers and executives, adding biometric authentication often makes sense to provide additional protection.
Tip: With FIDO2, it’s easy to allow employees to use multi-factor authentication. There are no new devices to buy and minimal need to provide training sessions.
3. Launch Multi-factor Authentication for High-risk Users
Due to their responsibilities, some users in your organization have more significant security needs than others do. For example, managers and software developers often require substantial access to do their work. If those access credentials fall into the wrong hands, the organization could suffer a significant loss. Consequently, we recommend focusing your initial multi-factor authentication implementation on these users.
4. Collect Feedback for Your Next Phase
After the initial MFA program is implemented, take a step back to evaluate how the program has unfolded. For instance, survey users to ask them which aspects of multi-factor authentication (MFA) they found most challenging. You may find that users didn’t understand why MFA was necessary. In that case, you can adjust your messaging to explain why MFA is needed in future iterations.
After You Launch Multi-factor Authentication, Do This Next
Fast multi-factor authentication contributes to protecting your organization. Instead of relying upon passwords exclusively, you’ll have additional layers of protection between you and threats. However, a full cybersecurity program requires much more than multi-factor authentication. A fully mature cyber program requires identity and access management, password policies, and training for employees. Without these in place, you’ll fall behind other organizations that have these elements in place.
You also need to set up IT security metrics so that you can track how your organization is performing. Finally, you always need to be looking for ways to make IT security easy for your employees to implement. One of the fastest ways to make IT security more convenient for employees is to implement an IT security chatbot that can handle password resets and security tasks around the clock.